Banking as a Platform (BAAP): Innovating Retail Banking
Banking as a Platform (BAAP), or platformification of banks is increasingly becoming an accepted business model for several banks to cultivate, monetize, and leverage APIs. BAAP or Platform Banking is not a new concept, a World Retail Banking Report by Capgemini explains. For example, a 2021 study by the European Banking Authority found that 97% of banks in the region used platforms to market and distribute products and services, while 83% reported exploring opportunities to use platform models to diversify and expand beyond their primary geographic markets.
India’s digital banking platform market was worth USD 776.7 million in the year 2021, according to BlueWeave Consulting Study. The study underscores that the market is estimated to grow at a CAGR of 9.8%, earning revenue of around USD 1,485.5 million by the end of 2028.
This growth of Banking as a Platform is attributed largely to faster digitization in the country. Another factor is the faster adoption of growing technologies like artificial intelligence (AI), cloud computing, the Internet of Things (IoT), and the use of APIs- all of which leads to automation in finance, higher customer satisfaction, and increased business revenue.
Bank’s CMOs, CIOs, and C-Suite executives can gain usable insights from this blog for building customer-led journeys and a data- and technology-driven product or service platform. But before we dive deeper into the subject, it is essential that we know what is Banking as a Platform or BAAP.
What is Banking as a Platform?
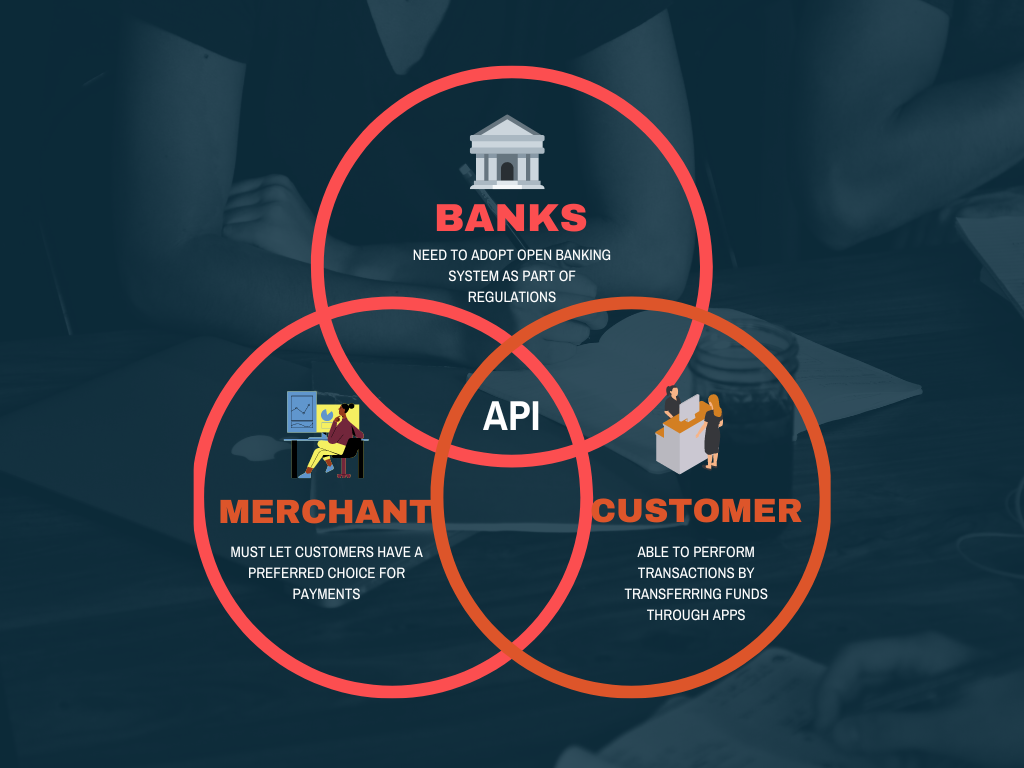
Banking as a Platform is defined as a business model where third-party developers build products or services for banks. These developers can be from a fintech or any other software/technology company, and they embed APIs into platform functionalities, while a banking platform can itself manage data exchanges, authentication, and compliance.
Is Banking as a Platform & Banking as a Service the same?
In layman’s terms, a fintech or any other software/technology company can develop a product or service and “rent” it to a bank. Banking as a Platform cannot be used interchangeably with Banking as a Service (BAAS) because banking institutions enable fintech and non-financial businesses to provide financial services in the latter. So these are two exact opposite terms. In fact, BAAP is a business model that fits perfectly into the modern-day financial ecosystem, where fintech companies can enable banks and work in conjunction rather than as two separate bodies, to enhance customer experience.
Banking as a Platform is hence, largely being accepted to embed banking into the broader ecosystem journeys of customers to empower inclusivity and sustainability. Banking as a Platform or BAAP is also known by other names like Platform Banking, Open Banking, and Ecosystem Banking.
Speaking specifically of India, the digital banking platform market is segregated into two types- based on their deployment. These include- on-premises and cloud segments. Cloud deployment of Banking as a Platform product has more market capture due to better traffic, faster access to data, and improved efficiency. Also, cloud deployment of BAAP offers faster rectification and tracking of issues, which in turn, reduces the risks of reputation damage.
A third of retail banking customers were interested in platform services offered by their primary lender, a Deloitte survey conducted in the United States said. 34% of customers surveyed said they were willing to use platform banking service they were willing to use platform banking services, whilst 25% said they were neutral.
Younger customers, both Gen Z and Millennials are more inclined towards financial superstore app, with an overwhelming 75% and 67% approval, respectively. 54% Gen X and 33% Boomers showed interest in a digital banking platform whilst on a cumulative level, 55% of all respondents had shown interest in India.
While prolific growth is highlighted in this business model across all geographies, there are still some reservations due to the traditional way of working. So why should banks consider BAAP?
Moving Past the Status Quo: Why Banks Must?
“The key question incumbents must ask themselves is whether banking is a destination or an enabler? As an enabler, banks can go beyond their products/ services and embed themselves within customers’ lives, paving the way for ecosystem banking,” says Christopher Young, Director, Financial Service Strategy, Adobe.
Banks that embrace Open Banking trends could profit from a potential revenue uplift of 20 percent, whereas those failing to do so risk losing 30 percent to disruption by the end of 2020, per one study from Accenture.
All parties are in a triple win-win situation when they adopt a BAAP model.
- Customers- They are still owned by banks, and by adopting a BAAP model they win because of better, newer, and tech-advanced services from banks.
- Banking as a Frontend- Banks win in this model because they can increase customer engagement, customer satisfaction, and revenue, while also saving development and support costs.
- Fintech- Fintechs are well integrated into the banking platform with the help of APIs. So, banks are powered by fintech companies. Meanwhile, fintech companies win because they can sell their product to a reputed and established institution for a profit.
Benefits of Banking as a Platform
Apart from focusing on the core business, banks can leverage platformification with major benefits as mentioned below:
- Reduced cost and time that goes into development of a product
- Maintenance costs are being borne by the fintech company or software development company
- BAAP introduces a new way of banking for customers, where they find new services
- Platform banking strengthens a bank’s position in the market
- Open banking or BAAP increases customer engagement and satisfaction
Banks can make use of the platform in a different way according to geographies, demography and market competitiveness. For example, in a highly competitive market or region, more importance is given to differentiation. So banks can have their SWOT analysis and build a platform or ecosystem around it. In a less competitive environment, BAAP can adopt the opposite strategy. It can become a one-stop shop by offering all possible services on a single platform.
RazorpayX: A Successful Use Case of India’s Neobanking Platform
RazorpayX is the neobanking platform belonging to the unicorn Razorpay. This neobank has already served more than 10,000 businesses- helping them process payroll using Opfin, paying expenses using a Corporate Card, and paying business vendors in real-time using the underlying payouts layer.
RazorpayX allows customers to open and operate fully functional current accounts, which come with standard banking features like debit cards, account statements, and cheque book. This platform has API banking capabilities, along with insightful reports, and approval workflow. RazorpayX also helps with automation in finance by refunding Cash on Delivery orders using Payout Links.
Future of Platform Banking
Embedded analytics will become the undercurrent of platform banking, along with key differentiators of AI and ML to enhance customer experience. The DNA of Banking as a Platform (BAAP) shall be defined through API strategy and how agile a bank is to fully use APIs.
While the future of BAAP or platform banking is still in a nascent phase, strong strategic planning and a roadmap can help trail retail banks’ path to a complete platform world. Hence, it’s a ripe time for the banks to consider consolidation for newer business models which would help them compete in the present business environment.
In our next blog of this two-part series, we put the idea of BAAP to the next level, explaining strategies for retail banks to compete in a platform world.